*Links & Tunnels to the outside
================================
While the relearn network is autonomous and not connected to the Internet, the relearn server is connected to two networks -- the relearn network as well as the Zinneke network that has access (via belgacom) to the Internet. One way to reach the public Internet is via the server & ssh.
links (the program)
---------
Start links by typing the command 'links' while connected to the server via *ssh*. Links is a interactive program (like man or less) and takes over the whole terminal. Press the 'g' key to *go* to a specific address. Use the up and down arrow keys to move through links and press return to follow links. The left and right arrow keys move back and forward in your history. Press the 'esc' key to open a *menu*. Press 'q' to *quit* links. Try 'man links' (from the shell) to get more information about how to use links.
ssh tunnel
--------------
Now that you have an ssh account with the server, and since the server is connected to the public Internet, you can use your ssh connection as a "tunnel" to reach the outside network. First, from the terminal, start an ssh session as before but with the -D (dynamic) option with a port number. This number will be your local connection to the tunnel.
- ssh -D 4321 username@10.9.8.7
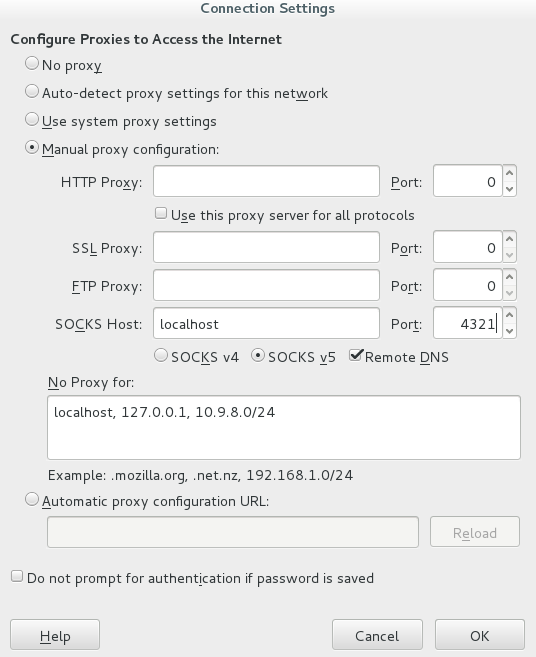
Then in Firefox (or other browser), you need to configure your connection to use a SOCKS proxy. In Firefox, this option is found via Preferences -> Advanced -> Network -> Connection: Settings...
MAKE SURE YOU CLICK Remote DNS!
FILL IN THE PORT YOU DEFINED ABOVE (4321 in this example)

../images/FirefoxSOCKS.png
This way of connecting is interesting for multiple reasons. When you tunnel via ssh, you're network traffic is encrypted. In this way, if you are using a hotspot that you don't fully trust, you can make sure that all of your traffic is encrypted. Also, your network traffic will appear as if it originates from your server; so by connecting to an ssh server is in another country, a tunnel could be used to circumvent filtering and blocking based on your geographic/national location.
HOW TO SAFELY QUIT USING SSH TUNNING WITHOUT BLOKKING THE PORT??
aka...> $bind: Address already in use
Socks Proxy on your terminal commands
You will need internet with cable, or your smartphone access point to download the proxychains app
on linux:
sudo apt-get install proxychains
then edit the file
add your tunnel port, look for the line [ProxyList]
- socks4 127.0.0.1 YOURPORT
on Mac:
use brew to install
- brew install proxychains-ng
- create on your home folder .proxychains folder
- mkdir .proxychains
- download the file
- edit tunnel port (at the bottom) of the follow file .proxychains/proxychains.conf
- socks4 127.0.0.1 YOURPORT
How to Use
- on linux
- proxychains YOURCOMMAND
- examples:
- proxychains apt-get update
- proxychains ipython
- proxychains python script.py
- on mac
- proxychains4 YOURCOMMAND
- examples:
- proxychains4 apt-get update
- proxychains4 ipython
- proxychains4 python script.py
*BLESS YOU*<3
Resources
------------
* [SSH Tunnel + SOCKS Proxy Forwarding = Secure Browsing ](http://embraceubuntu.com/2006/12/08/ssh-tunnel-socks-proxy-forwarding-secure-browsing/)
* [The black magic of ssh](The Black Magic Of SSH _ SSH Can Do That_-SD.mp4) [source](https://vimeo.com/54505525)
* [http://blog.trackets.com/2014/05/17/ssh-tunnel-local-and-remote-port-forwarding-explained-with-examples.html](http://blog.trackets.com/2014/05/17/ssh-tunnel-local-and-remote-port-forwarding-explained-with-examples.html)
* [SSH: The definitive guide](http://csce.uark.edu/~kal/info/private/ssh/index.htm